Portuguese Advanced Persistent Threats (APTs)
Portuguese Advanced Persistent Threats (APTs) represent sophisticated cyber espionage and cybercrime groups that have emerged from or have strong connections to Portuguese-speaking regions. These groups are characterized by their advanced technical capabilities, persistent nature, and strategic targeting of specific sectors.
Note: Attribution in cyber threats is complex and often uncertain. The information presented here is based on available threat intelligence and may evolve as new information emerges.

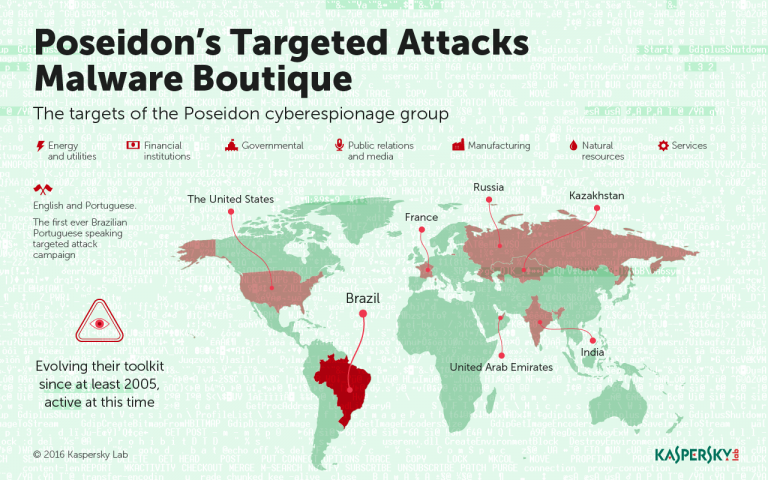
Source: Kaspersky Lab, 2016
The Poseidon Group is a sophisticated Portuguese-speaking Advanced Persistent Threat (APT) group active since at least 2005. First publicly reported by Kaspersky Lab in February 2016, the group is known for their unique operational methodology, combining cyber espionage with financial crime. Their approach involves three stages: compromise and data exfiltration, blackmail, and finally, approaching victims as a legitimate security firm offering remediation services. The group's activities span across multiple continents, targeting a diverse range of industries.
Primary Targets:
- Enterprise victims worldwide
- Financial institutions
- Government entities
- Domain and database servers
- Telecommunications companies
- Media and PR companies
- Manufacturing companies
- Energy and utility companies
- Healthcare organizations
Advanced Capabilities
Sophisticated technical skills and custom tool development
Strategic Targeting
Focused attacks on specific sectors and organizations
Global Reach
Operations extending beyond Portuguese-speaking regions
Organizations can protect themselves against these APT groups by implementing:
- Advanced threat detection and response capabilities
- Regular security assessments and penetration testing
- Employee security awareness training, especially regarding social engineering
- Strong access controls and network segmentation
- Regular updates and patch management
- Incident response planning and testing